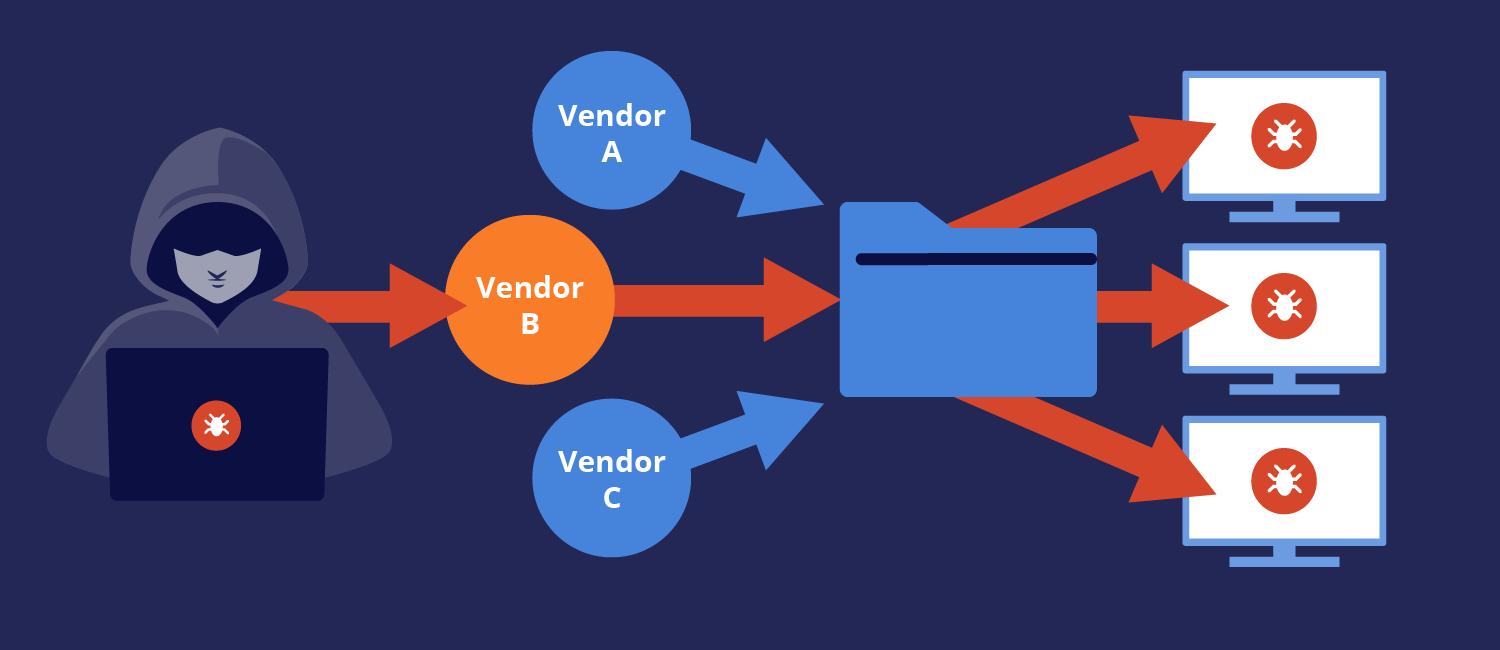
A supply chain attack is a cyber attack that targets an organization through its providers/vendors.
Current situation of supply chain attacks
A recent study shows that the supply chain attracts cyberattacks like a magnet. A whopping 97% of companies have been affected by supply chain attacks, with 93% of them admitting that they have been directly attacked due to vulnerabilities within the supply chain. According to an analysis by security provider Sonatype, these software supply chain attacks saw a staggering 650% increase in 2021, with Sonatype recording 12,000 incidents in the same year
“Supply chain attacks are terrifying because they are exceptionally challenging to deal with and because they demonstrate that you are placing your trust in the entire ecosystem,” said Nick Weaver, a security researcher at UC Berkeley’s International Computer Science Institute.
With a well-planned attack, they can disrupt a provider’s consumer network, resulting in hundreds or even thousands of victims. In addition, any firm that develops software or hardware for other organizations might be a potential target for these attackers.
Common supply chain attacks
- SolarWinds SUNBURST backdoor: On December 13, 2020, the SUNBURST backdoor was first revealed. The attack leveraged the widely used SolarWinds Orion IT management and monitoring software to develop a malicious trojan update. Its targets included services running Orion software and the U.S. Department of Commerce. Fortune 500 companies, telecommunications firms, other government agencies, and universities are also likely to be affected. Of particular concern within the SUNBURST backdoor was the targeting of dedicated servers, which are typically less frequently monitored. Preventing attacks like the SUNBURST backdoor requires constant monitoring at all levels of the corporate network.
- Exploiting vulnerabilities in Log4j: Another way of implementing a supply chain attack is by exploiting vulnerabilities in open source software. Notably, there was an attack where hackers exploited vulnerabilities in Log4j. This attack allows hackers to execute code remotely, including the ability to take full control of the server. Log4j is a zero-day vulnerability that was discovered by hackers before the software provider became aware of it. Since this vulnerability is associated with a part of the open-source library, it could potentially impact any of the 3 billion devices running Java.
- Attacks on Kaseya VSA Software: The primary goal of a supply chain assault is to exploit the weaknesses of suppliers in order to launch attacks on customers. That’s the method the Revil hacking collective employed when they targeted Kaseya VSA, a customer-facing remote monitoring and management service platform for IT infrastructure. By exploiting a vulnerability in the Kaseya VSA, REvil was able to send ransomware to 1,500 companies that are customers of Kaseya VSA.

- Capital One attack and cloud infrastructure security flaws: Not all cyberattacks originate from highly organized groups of hackers; in the case of Capital One (USA), a former Amazon employee used his insider knowledge of Amazon Web Services (AWS) to fraudulently charge $100 million to customer credit cards. The attack demonstrated the risks associated with cloud computing.
- Vulnerabilities on Personal and Third-Party Devices: In March 2022, American cybersecurity firm Okta disclosed that one of its vendors, Sitel, had been infected by a virus. via an employee using a laptop to perform customer service. Fortunately, the extent of the breach was limited, only two of Okta’s authentication systems were compromised, and no client data or settings were altered. However, through this incident, there is a risk that hackers would target devices belonging to subcontractors or employees who carry their own devices to launch more extensive attacks.
How to reduce the risk of cyberattacks on supply chains?
Cyber attacks are a constant threat, and every company and organization in the supply chain needs to be prepared for them. That’s why it’s so important for businesses to strengthen their network security defenses. Listed below is a remedy that institutions can do to shield themselves from and reduce the impact of cyber threats.
Carefully select your suppliers: It is imperative for businesses to verify that their vendors use certified security policies and infrastructure. This should be expressed explicitly in any cooperation agreement between the two parties.
Keep a close eye on software vendors: This is especially important for software with access privileges to company assets.
Restrict access to your data from third parties such as vendors and partners: Having fewer people with access to the data will make it easier to manage and prevent security breaches.
Safeguard the devices used by developers: Set up an endpoint protection platform and endpoint detection and response technologies to see any unusual activity and troubleshoot appropriately if necessary.
Education of staff, vendors, and associates: Organize training seminars to instruct workers on how to properly implement all of the company’s security measures, from password protection to technical assaults. All important matters should not be overlooked.
Always have a backup plan in unexpected cases: While no strategy can guarantee that a crisis won’t occur, you can prepare for it by having an event response plan ready to implement.
To ensure your clients’ faith and patronage of your services, VSEC is present 24/7 to improve the security of the IT infrastructure.
Source: ictvietnam, computerweekly, helpnetsecurity, gep.com