VSEC TI ENGINE – System for predicting, identifying incidents, risks of security loss
The security industry around the world is in a fierce battle against cyberattacks that are increasing in number, speed and complexity. This reality requires a new approach to preventing cyber threats. According to recent studies, traditional security solutions can almost exclusively identify known threats, while unknown threats are often difficult to identify. Therefore, VSEC TI Engine will help businesses collect data on cyber threats early, thereby improve efficiency and minimize the impact on business operations.
- What is VSEC TI Engine?
VSEC Threat Intelligence Engine (brand name: VSEC TI Engine) is a software solution for collecting, storing, and sharing structured cybersecurity metrics and threats in an efficient manner. VSEC TI Engine acts as a huge database of threats in cyberspace, constantly updated and optimized by VSEC’s team of experts to help customers’ information security team enrich threat data sources (URLs, IPs, files) of the business, thereby being able to proactively prevent the latest and complex threats early, minimizing the impact on business operations.
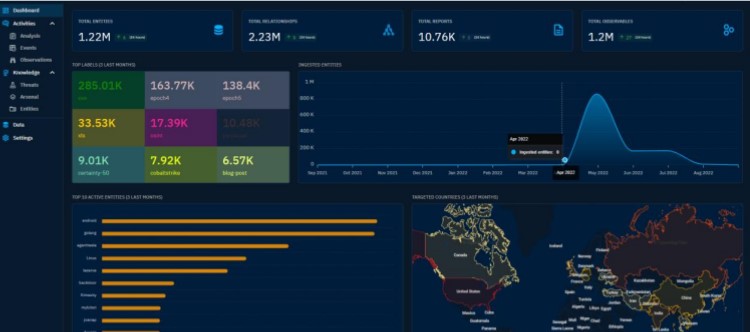
- Data is always updated 24/7 from many reputable malware prevention organizations, classifying threats according to customers’ fields.
- Research and closely monitor the activities of hacker groups around the world, provide relevant information before attacks take place.
- Integrate AI and Machine Learning enhances threat hunting.
- Significantly reduce response time to security incidents with threat insights collected before they occur.
- The rate of false positives is reduced by combining data collected from external sources with internal analysis data.
2. Main characteristics
- DATA COLLECTION
VSEC TI Engine receives data collected from many external sources (internet, SIEM software, SOAR or other threat intelligence platforms) and software data of VSEC TI Engine or collected from application DBs, device logs, crawl sources, … The collected data can be structured or unstructured.
- DATA NORMALIZATION
Data after collection will be standardized and pushed back to SIEM and SOAR through API connection to conduct monitoring and analysis thereby helping to find vulnerabilities, events, warnings.
- OPTIMIZE DATA STORAGE
All data is sorted, indexed, backed up when stored, fine-tuned to ensure no data loss.
- EASY EXPANSION
The software architecture supports flexible deployment. Easily scale your customer’s software horizontally.
The database management system supports the ability to run in parallel under the Cluster mechanism, allowing servers to be added if it is required to enhance performance without changing architecture and processing logics of application programs.
Link pdf: HERE


