In recent years, finding subdomains has become an important part of the pentest process. This mission usually takes time and effort. However, the development of digital technology platforms has provided us with effective tools. This article will outline 5 subdomain scanners to assist in the pentest process.
Outstanding methods for finding subdomains
The finding of subdomains helps in analyzing the domain infrastructure of any company. Let’s find out the most common uses of these tools.
DNS audit
DNS attacks are becoming more and more common, however, most companies are not aware of this threat. Very few companies perform DNS audit regularly although it brings more good things than bad ones. DNS audit can help find DNS vulnerabilities, and update and patch them. In addition, this process can find unused subdomains or potentially vulnerable ones.
Domain Intelligence
Red teams often use subdomain discovery took kit in their infosec investigations, which frequently include a number of OSINT techniques. These subdomain enumeration tools detect information exposed to the public such as information about users, apps, or technologies being used in the system.
Vulnerability scanning
An extensive list of domain names along with their subdomains can bring a lot of benefits to the process of vulnerability scanning
How subdomain scanners work
Querying search engines
We can use Google to search for subdomains of any domain. Just use the simple command line below:
site:vsec.com.vn -www
This command line will return all the domains indexed by Google.
Most of today’s tools use Google or Bing as built-in modules to assist in searching.
Performing brute force discovery
Some discovery tools use this method for improving search results. While it isn’t the quickest way to find subdomains, it can be one of the most accurate
TLS/SSL information
SSl/TLS certificates are not only useful for encrypting data sent and received between browsers and servers, but it’s also helpful for pentester.
Subject Alternate name (SAN) of SSL/TLS certificate can be used to extract domain and subdomain names
Top 5 subdomain scanners (terminal-based)
- AMASS
Developed on the Go lang platform, it’s one of the most effective tools in discovering large numbers of subdomain
AMASS uses a variety of subdomain mapping techniques including scraping, recursive brute force, reverse DNS sweeping, and Machine Learning to get the best result. Installing AMASS is quite easy. Installation instructions and manual are available at: https://github.com/OWASP/Amass
Or can install by using snap (on Kali Linux and other Linux distros), by a command line: snap install amass
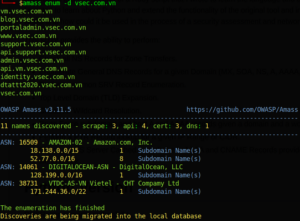
After installing, you can use the simple command below to search subdomain: amass enum -d example.com
Result:
User manual: https://github.com/OWASP/Amass/blob/master/doc/user_guide.md
- SubBrute
This is one of the fastest subdomain discovery tools. One of its coolest features is the ability to conceal the origin of the subdomain scanning itself, by using open resolvers as proxy to DNS rate-limit.
It can also work as a DNS spider that recursively crawls enumerated DNS records.
SubBrute supports filtering DNS records. For example, if you need to get only TXT records from any given domain name, you can use the –type option:
./subbrute.py -s google.names google.com –type TXT
Another great thing about SubBrute is the fact that it can be integrated into your own python scripts by using the subbrute.run() function. For example:
import subbrute
for d in subbrute.run (“yahoo.com”):
print(d)
For advanced usage, simply run: ./subbrute -h
- Sublist3r
Sublist3r is another Python-based tool that can be used as a massive subdomain scanner. It’s widely used by bug bounty hunters, as well as blue and red teams across the globe for subdomain data collection.
By querying search engines such as Bing, Yahoo, Google, Baidu, and other 3rd party sources like Netcraft or VirusTotal subdomain database, it can be one of the most effective and fastest tools around when you want to find subdomains.
Sublist3r minimum requirements are Python2 or Python3 versions.
Python 2 recommended version: 2.7.x
Python 3 recommended version: 3.4.x
To get started, you’ll need to clone the Git repo, and then run the installation for some of the dependencies with pip:
pip install -r requirements.txt
That’s it. Now you can perform subdomain scanning tasks:
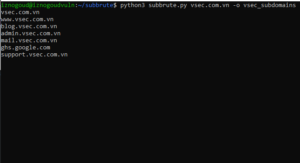
./sublist3r.py -d securitytrails.com
Expected output:
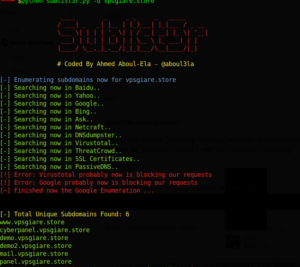
Github: https://github.com/aboul3la/Sublist3r
4. DNSRecon
DNSRecon is one of the most well-known domain reconnaissance scripts. As with almost every other one on this list, it’s written in Python.
It works by checking all NS records for AXFR zone transfers and can be very useful in DNS enumeration for almost any type of record, including MX, SOA, NS, TXT, SPF, and SRV.
It also supports wildcard resolution checking and brute force-based discovery for A and AAAA type-records with wordlists. It can also query Google Dorks to fetch indexed subdomains by GoogleBot.
After downloading the DNSRecon package, you’ll need to install a few required packages with pip:
pip install -r requirements.txt
Then you are ready to test it: :
./dnsrecon.py -d securitytrails.com
Result
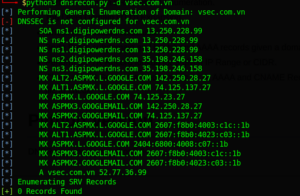
Github: https://github.com/darkoperator/dnsrecon
5. AltDNS
AltDNS is a subdomain discovery tool based on work with alterations and permutations.
By setting your own wordlist (or using the default wordlist at default altdns/words.tx), as well as using a list of confirmed subdomains, you can run the script to generate both altered or mutated results that may be present in the domain name.
It includes a dataset of 200+ subdomains that can be used to churn out valid subdomains.
After cloning the git project, install requested packages through pip:
pip install -r request.txt
Then you are ready to start using AltDNS:
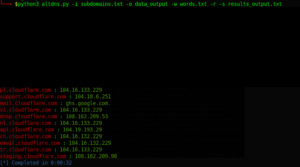
./altdns.py -i subdomains.txt -o data_output -w words.txt -r -s results_output.txt
Note: subdomains.txt is the actual subdomain list you know already exists, and words.txt is AltDNS’s own wordlist.
You can expect the output to look like this: