
On July 11, 2023, the webinar “Hack hackers with “multi-dimensional” defense tactics organized by The Vietnamese Security Network (VSEC) in collaboration with Vietnam Internet Association (VIA), took place successfully and leaving many good impressions in the IT community and small and medium enterprises in Vietnam. With useful sharing from experienced speakers in the industry, the webinar attracted the attention of more than 150 attendees.
The security story is not only for large businesses anymore, but regardless of the object, any business of any scale, whether it generates or owns large sources of data or liquidity, is the target of the company. cybercriminals for profit.
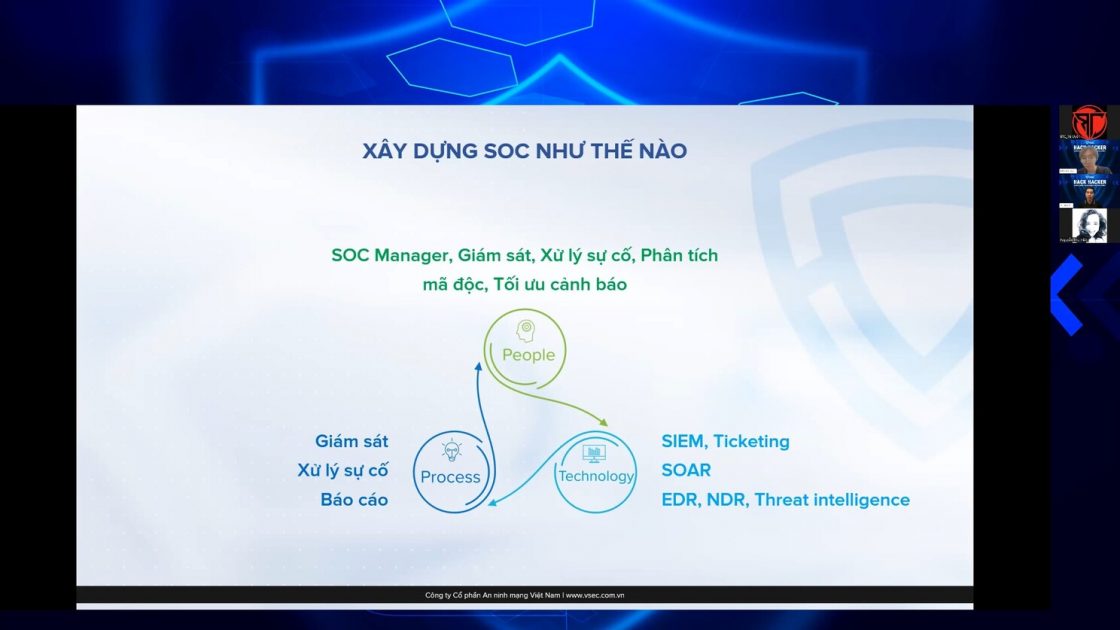
Monitoring information security in the enterprise
SOC is one of the security trends in the past 5 years. Large enterprises have equipped themselves, only a few small and medium enterprises pay attention to this issue. In his presentation, Mr. Vu The Hai – Head of VSEC Information Security Monitoring and Operation Center affirmed: “Information security solutions cannot prevent 100% of incidents. No solution provider commits that their solution can prevent all attack incidents.” Therefore, when system solutions, solutions, technologies and machines cannot be solved, we need to have a plan to detect and handle such attacks and incidents – that is by human means. People. At VSEC, SOC always ensures compliance with British CREST standards and other standards such as Azure.
Time to start SOC
Enterprises need to build SOC as soon as possible, should build immediately after having equipped with basic security solutions. At this time, the number of personnel, the amount of information and the processes just needs to be simple and moderate to suit the working environment.
It is not necessary to have a centralized SIEM system, a system to collect and analyze logs, you can directly use the portal of those solutions.
What do I need to prepare to work at SOC?
Webinar is not only for small and medium enterprises but also attracts a lot of students interested in working at SOC. To be able to work at the Information Security Monitoring Center, students need to master the basic knowledge: programming skills, system skills, application management and usage skills… Then , strengthen more specialized skills in SOC such as malware, web, common attacks, writing rules to detect malicious code….
Realistically react to Hackers using the Red Team method
The concept of Red Team (Deep Penetration Assessment) is very familiar in the international market. However, in Vietnam today, this concept is still not well understood and deeply understood, making businesses still hesitant to use Red Team.

With experience in participating in Red Team assessment for many domestic and foreign organizations for financial and banking units, etc., Mr. Be Khanh Duy – Head of VSEC’s Southern Regional Expert Service team said in the era Regarding the current development of network security, Red Team has become a trend in Vietnam, bringing many benefits to organizations and businesses. Before deploying Red Team, businesses need to plan and prepare thoroughly to ensure the process is efficient and brings the desired results. Here are some key steps businesses should take before implementing Red Team:
Identify goals: Clearly outline the Red Team’s goals and objectives. Identify specifically which part of your organization’s security infrastructure, processes, or people you want to evaluate and improve. Besides, it is also necessary to set the Red Team’s attack target, for example: Internet Banking system, Customer information,…
Scope and Rules of Engagement: Clearly define the Red Team’s scope, including the systems, networks, and applications that are in scope and those that are out limitations eg: Core-Banking system, no leadership Phishing,… Establish rules of engagement to ensure Red Team operates within legal and ethical boundaries.
Get Stakeholder Consent: Ensure approval and support from key stakeholders, including upper management, IT team, legal department, and any other stakeholders. They should be aware of the goals, benefits, and potential risks associated with Red Team exercises.
“Currently the cyber environment is no longer safe. For organizations that always put information technology security first, it is even more important to protect their company’s data assets. Therefore, using Red Team can increase the responsiveness of the organization and improve the defensive knowledge of your Blue Team team.” Mr. Be Khanh Duy affirmed.


