Hi, it’s time we meet again, I make a new blog at the end of the month. This time the theme will be a little different. Basically at the beginning of this June, after a year of so-called temporary graduation, I took the first security exam in my life, which was OSCP, and fortunately, without humiliating myself, I passed:’ >. So this post will be about my recent OSCP experience and the takeaways from it. Hope this information is useful
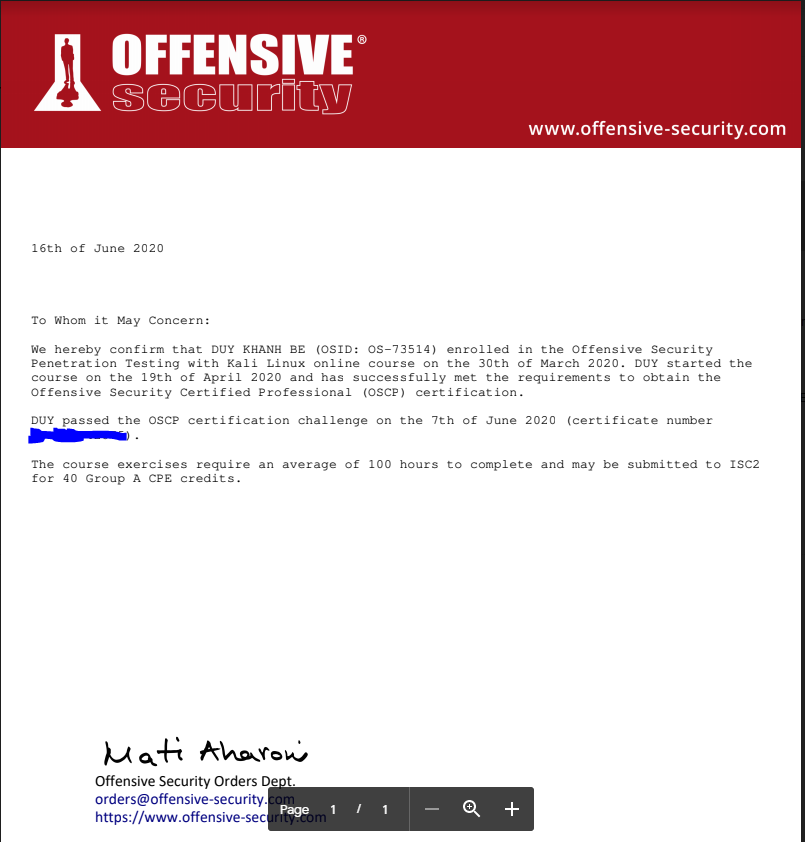
OSCP Examination
First of all, what is OSCP? Offensive Security Certified Professional (OSCP) is a certification program that focuses on security testing and attack skills. It consists of 2 parts: a pentest lasts within 23 hours and 45 minutes and a report submitted within 24 hours after that. OSCP is a very practical test.
So why should you take the OSCP test? I have 2 main reasons:
- To learn and improve knowledge and skills about security testing. As mentioned in the previous post, I just switched to Pentest recently, so I need something more oriented about this area. When you register for the test, you will be able to experience more than 54 very practical labs and have a very clear and specific set of instructions.
- To increase salary (of course). Last time, there was an article from Cyradar that said that OSCP certification helps increase salary by 200%. OSCP is now a rising certificate, because of its practicality and difficulty. It is ranked in the TOP 5 desirable and necessary pentest certificates for pentester. It will greatly increase your self-worth because besides CEH, this is a required certificate for many contractors.
The skills you will acquire through the OSCP course:
– Passive Information Gathering
– Active Information Gathering
– Vulnerability Scanning
– Buffer Overflows
– Working with Exploits
– File Transfers
– Privilege Escalation
– Client-Side Attack
– Web Application Attacks
– Password Attacks
– Port Redirection and Tunneling
– The Metasploit Framework
– Bypassing Antivirus
My OSCP journey
Let’s go into the main part of this article. I will cover what I went through in the OSCP course and what I learned (experience and advice).
Because the company requires a certain employee to have an OSCP certificate, and if that employee has one, they will get a salary raise =))) and I feel that I am quite predestined with all kinds of tests, so I accept it :v
The journey will be divided into 3 main stages:
Preparation stage:
There are a few things you need to prepare before you register for the test.
First is the information about the certification, You must know what you are taking and what the test format is, right? It will be located here https://support.offensive-security.com/oscp-exam-guide/.
Second is the necessary knowledge and skills. When you register for the test, you will have to buy a package that includes the exam fee, Penetration Pentesting with Kali Course includes an 800+ page PDF and over 8 hours of video tutorials, and a VPN to connect you to the lab environment (the most valuable in the package). For Lab, you can buy 30-day, 60-day, or 90-day types depending on your intentions. I chose 60 days. Because time is money, before you buy this package, you need to prepare the right knowledge and spirit, otherwise, you will be overwhelmed (like me) in terms of knowledge and skills, and in those 60 days, I’m sure you will not have enough time to practice enough for the test. Because at school, I have been taught and practiced these things, I am quite familiar so I am not surprised.
So what you need to prepare in terms of knowledge is:
- Linux and Windows environments. This is what I consider the most important. You need to have knowledge and familiarity when working with both Windows and Linux environments, especially Command Line Interface on Linux because that’s where you work the most, especially Kali. If you are new, this book may come in handy: Kali Linux Revealed.
- Basic programming skills. This includes reading, understanding, and being able to modify Python, Bash, Perl code, etc. You won’t need to write a complete exploit, but you should at least understand how it works. There are millions of websites out there that can help you get familiar with Python. Before I jumped straight into it, I didn’t have a very useful method :v
- Web Application Attacks (SQLi, Local File Inclusion, Remote File Inclusion, Command Injection, …), In the labs you will have to exploit mainly Web Applications, so you need to have a certain understanding of these types of attacks. Web Application Hackers Handbook, this book is very useful for those who are new to this problem.
- Tools that run on Kali/Linux: The last thing is that you need to be familiar with or at least know how the tools work – which you need to rely on to be able to complete the test. Some tools you need to know are Metasploit, Nmap, and Netcat.
- Get familiar with the lab environment: To avoid being surprised when attacking a computer. You can familiarize yourself with the labs similar to OSCP on Hack The Box, or refer to the link here OSCP Like Vulnerable Machines List by abatchy.
Before taking the test stage:
Once you’re confident and mentally prepared, you can register to get started on the Offensive Security homepage. After you sign up for the lab term, on the day you sign up, you’ll receive an email with course materials and instructions for connecting to the lab environment.
I don’t know about you, but I always have the habit of having basic knowledge first, knowing what I have to do before I start doing it. So I divided this stage into 2 parts, theory and practice.
Theory:
I spent almost the first month just reading and studying the material provided. It includes an 800+ page PDF book and a set of accompanying visual videos. There are also Exercises in the book at the end of each section, if you do all the work and submit the reports you will get 5 extra points of attendance on the final test result. My opinion about the document is that it is very complete, it is designed so that a complete beginner can get the most basic knowledge, and it is also very broad and comprehensive in all areas. If there is no preparatory stage, you will really be overwhelmed by the amount of information it brings.
My advice and experience is that you may not need to see and know the whole thing, but you should read it once. You can skip the parts you think you already know, and read the parts that feel new to you. Because there are information and tools in the material that are very good and useful, which will directly help you do the lab exercises and tests easier.
Practice:
This is the most valuable part of the whole package, according to the comments of most people. Because this is what helps you prepare for your test, it can also serve as a sample question.
There are a total of 57 public servers for you to attack, and in addition, there are 3 internal servers that you can pivot to when you get the keys from a certain public computer. During the lab time, I was able to root about 52/57 computers.
My learned experience is that:
- You should start with Alpha and Beta machines first, with IPs of .71 and .72. Because these are samples, there are sample reports on the student’s forum that are very detailed on the approach and methodology to attack and gain permission to a server.
- There are 2 keywords you always need to remember which are “Enumerate more” and “Try Harder”. Really after you finish this one, you’ll definitely stick to these two phrases, because they’re the keywords every time you get stuck somewhere. Sometimes it’s only a hidden port away before you find the answer or sub-directories that you haven’t enumerated yet. Regarding enumerations, I found a pretty good and detailed tool that helped me with one computer for the final test: https://github.com/Tib3rius/AutoRecon.
- Always take note of what you find and achieve. I have an Excel file to record what I enumerated, as well as the exploit code I used to exploit and gain permission. Because there are some computers that require you to hack into another machine in order for you to access it. This will make it easier to go back to that computer and know the link between each computer to go back to.
- You can refer to the student’s forum for instructions if you are stuck somewhere for too long. There are posts to discuss each computer, or you can also inbox your fellow test takers for more approaches. However, you should not abuse it, because you will not have it when you take the test.
- Always revert a computer before doing it. Because you are not the only one accessing that lab environment. You should revert to what others have done on it before to make sure the environment is as clean as possible.
On the test day:
Before the test day, you should prepare very carefully, both physically and mentally. Because it’s a 24-hour test. No help, no suggestions, just you and your supervisor.
Prepare your health, food, and drink plan you need to complete the test. Get enough sleep. For the duration of the test, you are allowed to leave your seat, move around, and rest. Don’t stress when you’re stuck somewhere, stop, pause, or switch to another computer. Never let stress, panic, and anxiety take over your mind. On the test day, during the first 12 hours, I didn’t have a shell on a single computer, everything was missing a tiny bit, and I swear you don’t know how much I swear on this question. After 3/4 of the time, it improved a bit when I finished each Buffer Overflow exercise (similar to drawing a function graph in the university entrance exam). But after I went out to breathe for about 20 minutes, I came back and suddenly I saw something I hadn’t seen before, and I found my reel again. As a result, I finished the test with only 1 computer that could not be rooted. One result I know is more than enough to pass. From there, I understood the two spells “Enumerate more” and “Try Harder”.
Within the next 24 hours, you must complete and submit a report, about the enumeration process as well as how you exploit and gain permission. The report requires specific screenshots and instructions to reproduce, so you must make sure to take pictures of the steps during the test, because when you finish the test, the VPN connection will be disconnected, and no there will be no chance for you to connect to the server to do it again.
And finally, after submitting the reports, the results will be available within 10 working days. And when the results come, yayyy, I finally have a chance to get a salary raise =))))
Conclusion
And in both the study and test process, always find enjoyment. There’s always a certain happiness either small or big when you learn something new, something that makes you surprised, or when you successfully root a computer that took you days to do. :’> So have fun.
Be Duy ( aka chalizard )























 Mr. Dao Hoang Duong – Deputy Head of EVN’s Department of Telecommunications and Information Technology gave the opening speech
Mr. Dao Hoang Duong – Deputy Head of EVN’s Department of Telecommunications and Information Technology gave the opening speech


 Serious and urgent atmosphere of the practical exercises
Serious and urgent atmosphere of the practical exercises



