General News
PRESS RELEASE: VSEC Sponsors Vietnam’s First National Student Cybersecurity Competition
Hanoi, October 18, 2025 – In the days leading up to the signing ceremony of the United Nations’ Hanoi Convention on Cybercrime, a historic milestone underscoring Vietnam’s strong commitment to global cybersecurity, The Vietnamese Security Network JSC (VSEC) — one of the first and longest-standing cybersecurity enterprises in Vietnam — once again demonstrates its leadership by sponsoring the first-ever Cybersecurity Student Contest Vietnam. 22 Years of Growth…
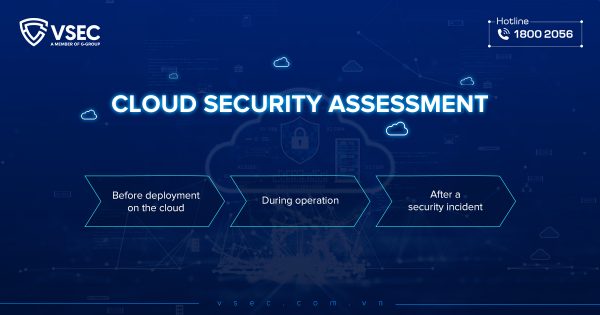
Security assessments seen as key to protecting businesses in the cloud
VSEC warns rising cloud security incidents in Vietnam demand timely assessments to protect businesses before deployment, during operations, and after incidents. According to Vietnamese Security Network (VSEC)’s 2024 Cybersecurity Situation Summary Report, 27% of organizations recorded cloud security incidents in 2024, with over 80% of cloud vulnerabilities exploited due to misconfigurations or lack of monitoring.…
390,000 WordPress accounts stolen in year-long attack campaign
The hacker group MUT-1244 has conducted a year-long campaign, stealing 390,000 WordPress login credentials along with many other sensitive data by using trojanized GitHub repositories to spread malware. These repositories were embedded with malicious code to steal WordPress credentials along with SSH keys and AWS access from victims, including security researchers, red team members, testers,…
Rootkit PUMAKIT: A new threat on Linux with advanced stealth techniques
Security researchers have uncovered a new Linux rootkit named PUMAKIT, featuring capabilities such as privilege escalation, file and directory hiding, and self-concealment from system tools to avoid detection. According to a report from Elastic Security Lab, PUMAKIT is an advanced Loadable Kernel Module (LKM) rootkit that leverages modern stealth mechanisms to maintain persistent connections with…
Passkeys: Microsoft’s solution to 7,000 password attacks per second
Microsoft is ushering in a new era of authentication with passkeys—a modern, secure, and convenient alternative to traditional passwords. According to statistics, Microsoft blocks up to 7,000 password attacks per second, double the rate from the previous year, while adversary-in-the-middle phishing attacks have surged by 146%. Passkeys offer a robust phishing-resistant solution by leveraging biometric…
Google pays $55,000 for a Critical Chrome Vulnerability with Remote Code Execution (RCE) potential
Google has released a major update for its Chrome browser, addressing three security vulnerabilities, including two high-severity memory safety flaws reported by external researchers. The most notable flaw, CVE-2024-12381, is a type confusion vulnerability in the V8 JavaScript engine, which earned the researcher who discovered it a $55,000 reward. Google stated that this flaw could…
Cisco releases patch for critical URWB vulnerability in Industrial networking systems
Cisco has issued security updates to address a critical vulnerability affecting Ultra-Reliable Wireless Backhaul (URWB) Access Points, which allows unauthenticated remote attackers to execute commands with root privileges. Ultra-Reliable Wireless Backhaul (URWB) is a highly reliable wireless transmission technology, commonly used to connect components within network systems, particularly in 5G mobile networks and industrial networks.…
Canada orders closure of TikTok
The Government of Canada has mandated the dissolution of TikTok Technology Canada, a subsidiary of ByteDance, due to concerns regarding national security risks. However, this decision does not impose a ban on users, allowing them to continue accessing and using the platform without interruption. This action follows comprehensive national security assessments, including close scrutiny from…
Microsoft releases patch addressing 90 new vulnerabilities
Recently, Microsoft announced two security vulnerabilities in Windows NT LAN Manager (NTLM) and Task Scheduler that are actively being exploited in the wild. These vulnerabilities are part of a total of 90 security flaws that the technology giant addressed in the November 2024 Patch Tuesday update. Among these, four vulnerabilities are classified as Critical, 85…
Russian hackers exploit new NTLM vulnerability to distribute RAT Malware via Phishing emails
Recently, a new security vulnerability in Windows NT LAN Manager (NTLM) has been exploited by hackers suspected to have ties to Russia, as part of cyberattacks targeting Ukraine. This vulnerability, tracked under the identifier CVE-2024-43451 (with a CVSS score of 6.5), allows attackers to spoof and steal NTLMv2 Hash Disclosure information from users. Microsoft issued…
Over 30 critical security flaws discovered in open source AI and ML Models
Cybersecurity researchers have identified more than 30 security vulnerabilities across various open-source artificial intelligence (AI) and machine learning (ML) models. These vulnerabilities could potentially lead to remote code execution and the theft of sensitive information. Details about these vulnerabilities were reported through the Huntr bug bounty platform by Protect AI, affecting several tools including ChuanhuChatGPT,…
Microsoft wants $30 fee for delaying upgrade to Windows 11
Microsoft has announced that Windows 10 users can postpone their transition to Windows 11 for an additional year by paying $30 for the Extended Security Update (ESU) program. This marks the first time the company has disclosed the price for this service, following its announcement of the program in December 2023. According to Microsoft, support…