Our clients are those who operate in the banking sector. In line with the trend, they are actively developing online software utilities to provide more convenient services for current clients as well as expand their new client network. These utilities is often accompanied by security risks. VSEC’s VCHECK penetration testing service visually demonstrates the significant risks of an online banking application. They may arise from the potential for a valid user to proactively access the full bank account information of other clients.
About clients
Our client is a joint-stock commercial bank in the Top 1000 largest banks in the world, with total assets of nearly USD 6 billion and more than one million regular active accounts. After nearly 25 years of operation, this bank has been frequently awarded prizes such as EuroMoney, Asian Banker, The Banker, and so on from prestigious international organizations.
Challenge
To enhance transaction convenience, the bank has developed a Mobile Banking application on mobile phones. Through this software, clients can query and conduct basic transactions similar to when they do so at a teller counter. At the time of assessment, over 1.06 million bank accounts have been activated and regularly used. The service development has posed challenges regarding information security assurance. Bank account numbers are considered non-confidential information. When conducting online transactions, many users provide them on websites for transferring money to buy and sell goods and services However, certain account-related financial details must always be protected at the highest level: account balance, transaction information, etc. Securing this information is the responsibility of the bank which provides the technological infrastructure. In the home country, the state bank has also issued many strict regulations that bind banks to comply with and ensure information security, such as BASEL, PCI/DSS, and so on. Due to handling multiple tasks with a heavy workload, technical personnel often lack the necessary resources, time, and skills to carry out information security assessments and testing. As regulations become increasingly specific, banks are required to ensure proper compliance and consistently maintain control checks.
Solution
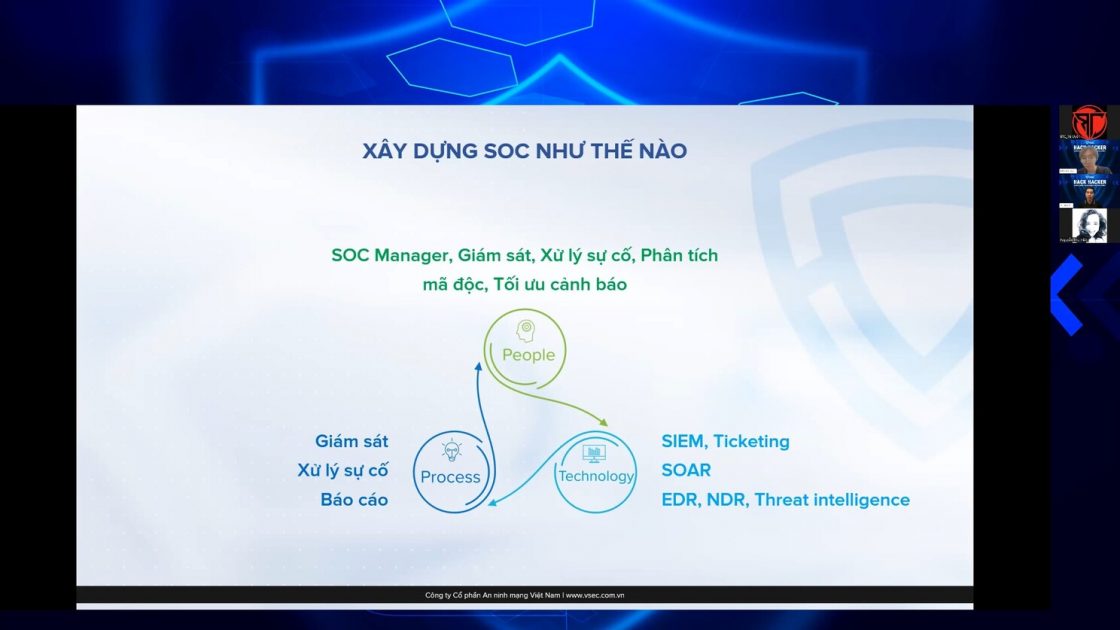
One of the biggest concerns of banks is whether the Mobile Banking application that is provided to clients is safe or not, and how well user data is protected. As a result, the bank needs to use an information security penetration testing service to obtain objective and multidimensional information. VCHECK is VSEC’s overall information security service, which includes penetration testing. The service is capable of imitating the most realistic way that external attackers take advantage of the vulnerability to illegally collect Client’s data. To begin the penetration testing process, the Bank provides VSEC the name of the Mobile Banking application on the Google Play (Android version) or Apple Appstore (iOS version). VSEC technicians will act as attackers and imitate real-life techniques in order to identify software vulnerabilities. Skilled engineers combined with various specialized tools will learn how the Mobile Banking application works and how the server interacts with the application to detect weaknesses, reconstruct security errors and finally report. After 10 days, a VSEC engineer establishes a bank account as a customer of the bank. With the key technique of using a proxy, it assists the engineer in fully comprehending how the application works and how it interacts with the Bank’s server. The application includes many different components, VSEC engineer noticed a serious issue while allowing him to view the details of any other account. This serious security error occurred because computer programmers did not closely apply to user account management and safe programming standards. VSEC have transferred the entire implementation process to the Client. Simultaneously, VSEC recommended to remedy it by modifying the application and providing the ability to verify whether the query submitted to the server is valid, and the correct information of the client is using or not.
Benefits of VCHECK security testing service
Deployment is quick and Clients do not need to provide much information.