In the dictionary universe of security assessment forms, Penetration Testing and Vulnerability Assessment are considered to be the two familiar and typical techniques that are most used. Although the functions, methods and implementation techniques may be different, in terms of final results, both methods aim to evaluate the security strength of the system.
To make it easier for businesses to choose which form of security assessment is more suitable for them, we will list some basic differences as below.
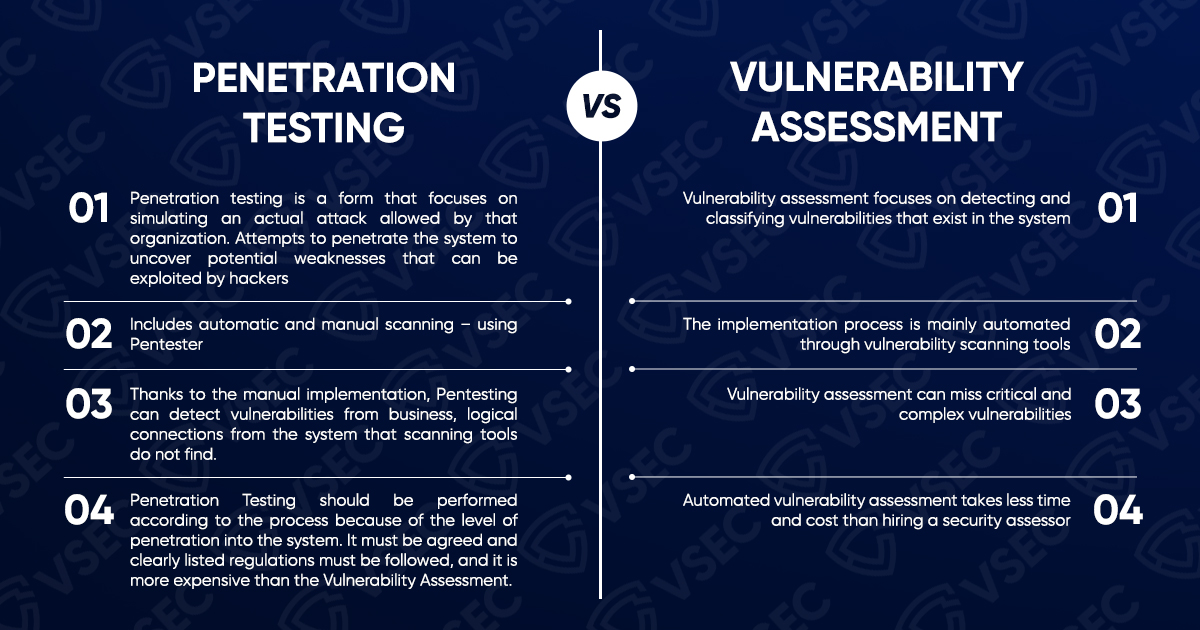
The difference between Penetration Testing and Vulnerability Assessment (Source: VSEC)
What is Vulnerability Assessment (or VA)?
True to its name, VA is a form of security assessment through which businesses can find the most possible vulnerabilities. With a VA, the organization will respond to cyber-attacks on the system by identifying, classifying and resolving security risks and guiding to minimize the risks in the best way.
Recommendation: The unit in charge of the VA may not have specialized personnel or the management system may not be equipped with many security tools, but it may have identified the goal of checking for vulnerabilities in the system for appropriate recommendations.
The basic form of VA that these units perform often focuses on security assessment on websites, applications, etc and the business’s information technology infrastructure.
Why Vulnerability Assessment is needed?
All information security experts recommend that businesses need VA as soon as possible because the core value system of the businesses needs to be ensured the maximum level of security before expanding or upgrading in line with the speed of business development. Here are four basic reasons:
Firstly, VA helps identify threats and weaknesses in IT system security early
Secondly, after VA, the IT department will need to take corrective actions to close vulnerabilities and protect sensitive information systems.
Thirdly, VA helps businesses implement and meet compliance requirements, and applicable cybersecurity regulations such as HIPAA and PCI DSS.
Fourthly, VA helps protect against data breaches and unauthorized access
Only if a business has a dedicated security or information management team, should it perform Penetration Testing?
Not entirely correct. The assessment and testing by security experts will be a form of assessment that goes quite deeply into the business’ IT system in order to detect potential weaknesses and assess the security level of the system. There are many models and methods of security assessment for businesses to choose to minimize the risk of breaking the system’s security structure such as Pentest As A Service, Network Pentest, Web Application Pentest, Mobile Application Pentest, API. Pentest, etc..
In most cases, businesses that need to test their team’s defenses will choose Penetration Testing or even Red Team to test the system’s capabilities and professional qualifications of the staff themselves.
However, whichever form may be selected, businesses need to set clear goals, principles and limits for the form of an attack to ensure risk management during the security assessment.



