Recently, a new security vulnerability in Windows NT LAN Manager (NTLM) has been exploited by hackers suspected to have ties to Russia, as part of cyberattacks targeting Ukraine.
This vulnerability, tracked under the identifier CVE-2024-43451 (with a CVSS score of 6.5), allows attackers to spoof and steal NTLMv2 Hash Disclosure information from users. Microsoft issued a patch for this vulnerability earlier this week. According to information from Microsoft, minimal user interaction with the malicious file, such as clicking, moving, or deleting, can trigger the vulnerability without the need to open the file.
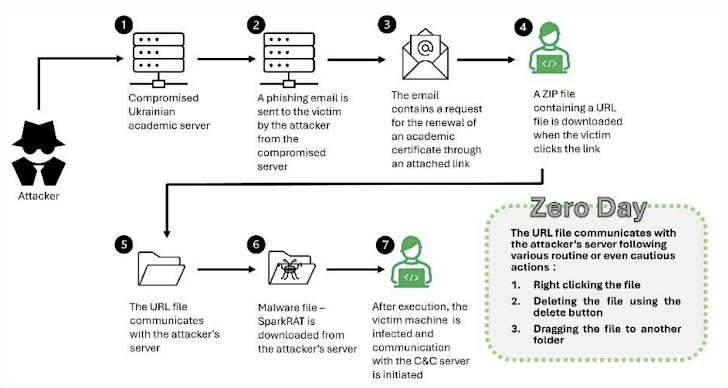
The Israeli cybersecurity firm ClearSky discovered this vulnerability in June 2024 and reported that it has been utilized in a malware distribution campaign involving Spark RAT, which exploits malicious URL files.
In this campaign, hackers sent phishing emails from a compromised Ukrainian government server, requesting recipients to renew their academic certificates through a trap link. When users clicked on the link, they downloaded a ZIP file containing a malicious internet shortcut file (.URL). The vulnerability is triggered when users interact with this file without opening it, such as by right-clicking.
The URL file is designed to connect to a remote server, from which additional malware, including Spark RAT, is downloaded. ClearSky also reported alerts regarding the transmission of NTLM Hashes via the Server Message Block (SMB) protocol. Once the attacker obtains the NTLM Hash, they can execute Pass-the-Hash attacks to access user accounts without needing a password.
The Ukrainian Computer Emergency Response Team (CERT-UA) has identified this activity as linked to a Russian hacker group designated UAC-0194. Additionally, CERT-UA has warned about phishing emails related to tax matters, which have been used to distribute remote access software known as LiteManager. They believe this attack campaign is financially motivated and executed by the hacker group UAC-0050.
CERT-UA has cautioned that accountants working with remote banking systems are particularly vulnerable. Investigations have shown that the time from the initial attack to the moment funds are stolen can be less than an hour.