
Today, WordPress is one of the most popular website-building tools all over the world, and it is no exception in Vietnam. Data thieves will naturally direct their attention here. Consequently, its plugin – Elementor Pro – has been exploited by malicious cybercriminals who are taking advantage of a security flaw that was just patched with the intention of stealing sensitive information.
This flaw, identified as a flawed access control situation, is present in 3.11.6 and earlier releases. In the plugin’s latest version, 3.11.7, released on March 22nd, the issue was fixed.
The Tel Aviv-based firm claimed in its release notes, “Improve code security enforcement in WooCommerce components. It is estimated that over 12 million websites use the premium plugin. An authenticated attacker can completely take over a WordPress site with WooCommerce functionality if they are able to exploit this highly critical vulnerability.”
“A malicious user only needs to turn on the sign-up page (if it’s off) and change the default user role to admin and they can instantly create an account with administrative privileges. With this authority, they can “redirect the site to another malware domain, upload an unauthorized plugin, or backdoor, and further exploit the site” Patchstack claimed in a warning released on March 30th, 2023.
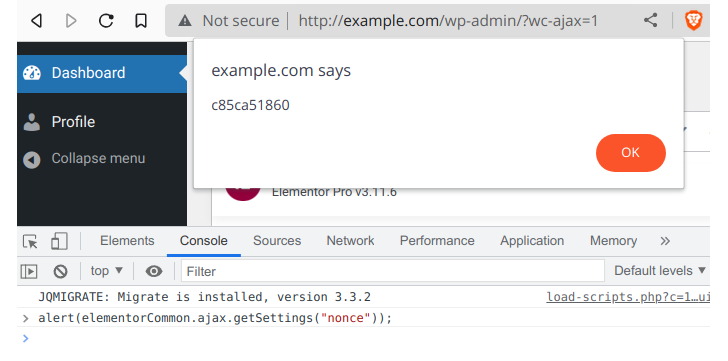 Patchstack also reports that the flaw is being exploited from many IP addresses in an attempt to upload arbitrary PHP and ZIP packages. Users of the Elementor Pro plugin should upgrade to version 3.11.7 or the most recent version, 3.12.0, as soon as possible to protect themselves from security breaches.
Patchstack also reports that the flaw is being exploited from many IP addresses in an attempt to upload arbitrary PHP and ZIP packages. Users of the Elementor Pro plugin should upgrade to version 3.11.7 or the most recent version, 3.12.0, as soon as possible to protect themselves from security breaches.



